Using ECS Exec with read-only root file system containers
UPDATED 2024-08-31: Make the workaround work for the Fargate Platform Version 1.4.
As stated in the official ECS Exec documentation, ECS Exec today doesn’t support read-only containers.
The SSM agent requires that the container file system is able to be written to in order to create the required directories and files. Therefore, making the root file system read-only using the readonlyRootFilesystem task definition parameter, or any other method, isn’t supported.
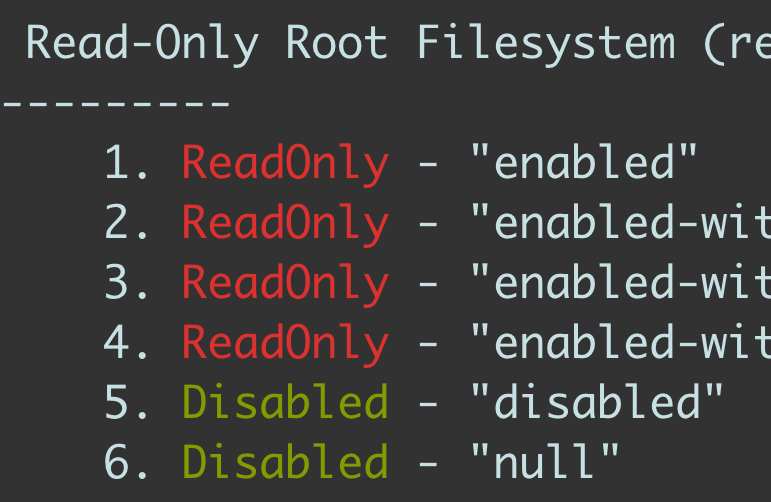
This limitation means that you cannot use the readonlyRootFilesystem ECS task definition parameter enabled in your ECS tasks, so the amazon-ecs-exec-checker1 prints errors for this configuration enabled as shown in the cover image above.
While ECS Exec (or the SSM agent more specifically) doesn’t support it for the rationale reason, some users want to use ECS Exec with read-only container storage for good reasons2.
Note that because the ways I’ll show you below are just “workarounds” and of course they’re not officially supported by AWS, the workarounds could easily stop working by any changes made in Amazon ECS or in the SSM agent in the future.
TL;DR;
In summary, the workarounds I’m going to describe in this article are basically do the same thing - creating two explicitly writable directories, more specifically /var/lib/amazon and /var/log/amazon, for the SSM agent.
So make sure that you at least need to allow the agent to write to those directories, and the workarounds may not suit for you if you want to keep having fully read-only containers.
Implementing workaround
You can choose one of the two ways below to create writable directories
Starting from the Fargate Platform Version 1.4 (as explained in this GitHub issue comment3), the following steps are both required to make the workaround work:
- Define volumes in
Dockerfile - Define volumes in ECS task definition
1. Define volumes in Dockerfile
Here is an example of Dockerfile. See the line 3-5 and 7-9. (The base image alpine:3.13 does not matter here of course).
| FROM alpine:3.13 | |
| RUN mkdir -p /var/lib/amazon | |
| RUN chmod 777 /var/lib/amazon | |
| VOLUME /var/lib/amazon | |
| RUN mkdir -p /var/log/amazon | |
| RUN chmod 777 /var/log/amazon | |
| VOLUME /var/log/amazon |
2. Define volumes in ECS task definition
This is a bit complicated than the previous Dockerfile example, but you don’t have to modify your existing Dockerfile or container images if you take this approach.
Here is an excerpt of an example ECS task definition. The important lines are:
- Line 2-5: Define Bind mount volumes
- Line 12-23: Mount the defined volumes
| { | |
| "volumes": [ | |
| { "name": "var-lib-amazon" }, | |
| { "name": "var-log-amazon" } | |
| ], | |
| "containerDefinitions": [ | |
| { | |
| "name": "task-def-level-workaround", | |
| "readonlyRootFilesystem": true, | |
| "image": "alpine:3.13", | |
| "command": [ "sleep", "1000000" ], | |
| "mountPoints": [ | |
| { | |
| "readOnly": false, | |
| "containerPath": "/var/lib/amazon", | |
| "sourceVolume": "var-lib-amazon" | |
| }, | |
| { | |
| "readOnly": false, | |
| "containerPath": "/var/log/amazon", | |
| "sourceVolume": "var-log-amazon" | |
| } | |
| ] | |
| } | |
| ], | |
| ~~ snip ~~ | |
| } |
Test it in your AWS account
You can create an ECS task definition using the “workarounds-included” CloudFormation template below to test in your AWS account.
There are three containers defined in the task definition for simplicity:
(bold texts are the container names)
- disabled - The
readonlyRootFilsystemoption is disabled for this container. So you can exec into this container without any workaround (of course.) - enabled - The
readonlyRootFilsystemoption is enabled for this container and there’s no workaround in it. So you cannot exec into this container. (The SSM agent won’t run for this container.) - enabled-with-workaround - The
readonlyRootFilsystemoption is enabled and the workaround is implemented. You’ll be able to exec into this container.
| AWSTemplateFormatVersion: "2010-09-09" | |
| Description: "CloudFormation template that represents a task on Amazon ECS." | |
| Parameters: | |
| ContainerImage: | |
| Type: String | |
| Default: "public.ecr.aws/toricls/alpine:3.13" | |
| ContainerImageWithWorkaround: | |
| Type: String | |
| Default: "public.ecr.aws/toricls/ecs-exec-workaround-readonly-fs-with-volumes:latest" | |
| Command: | |
| Type: CommaDelimitedList | |
| Default: "sleep, 1000000" | |
| LogGroupName: | |
| Type: String | |
| Default: /ecs/readonlyRootFilesystem | |
| Resources: | |
| TaskDefinition: | |
| Type: AWS::ECS::TaskDefinition | |
| Properties: | |
| Volumes: | |
| - Name: "var-lib-amazon" | |
| - Name: "var-log-amazon" | |
| ContainerDefinitions: | |
| - Name: "disabled" | |
| ReadonlyRootFilesystem: false # disabled | |
| Image: !Ref ContainerImage | |
| Command: !Ref Command | |
| LogConfiguration: | |
| LogDriver: awslogs | |
| Options: | |
| awslogs-region: !Ref AWS::Region | |
| awslogs-group: !Ref LogGroupName | |
| awslogs-stream-prefix: "disabled-" | |
| Essential: true | |
| - Name: "enabled" | |
| ReadonlyRootFilesystem: true # enabled | |
| Image: !Ref ContainerImage | |
| Command: !Ref Command | |
| LogConfiguration: | |
| LogDriver: awslogs | |
| Options: | |
| awslogs-region: !Ref AWS::Region | |
| awslogs-group: !Ref LogGroupName | |
| awslogs-stream-prefix: "enabled-" | |
| - Name: "enabled-but-with-workaround" | |
| ReadonlyRootFilesystem: true # enabled | |
| Image: !Ref ContainerImageWithWorkaround | |
| Command: !Ref Command | |
| LogConfiguration: | |
| LogDriver: awslogs | |
| Options: | |
| awslogs-region: !Ref AWS::Region | |
| awslogs-group: !Ref LogGroupName | |
| awslogs-stream-prefix: "enabled-with-workaround-" | |
| MountPoints: | |
| - SourceVolume: "var-lib-amazon" | |
| ContainerPath: "/var/lib/amazon" | |
| ReadOnly: false | |
| - SourceVolume: "var-log-amazon" | |
| ContainerPath: "/var/log/amazon" | |
| ReadOnly: false | |
| Family: "ecs-exec-workaround-readonly-root-fs" | |
| RequiresCompatibilities: | |
| - "FARGATE" | |
| - "EC2" | |
| NetworkMode: awsvpc | |
| Cpu: 512 | |
| Memory: 1024 | |
| ExecutionRoleArn: !Ref ExecutionRole | |
| TaskRoleArn: !Ref TaskRole | |
| ExecutionRole: | |
| Type: AWS::IAM::Role | |
| Properties: | |
| AssumeRolePolicyDocument: | |
| Statement: | |
| - Effect: Allow | |
| Principal: | |
| Service: ecs-tasks.amazonaws.com | |
| Action: 'sts:AssumeRole' | |
| ManagedPolicyArns: | |
| - 'arn:aws:iam::aws:policy/service-role/AmazonECSTaskExecutionRolePolicy' | |
| TaskRole: | |
| Type: AWS::IAM::Role | |
| Properties: | |
| AssumeRolePolicyDocument: | |
| Statement: | |
| - Effect: Allow | |
| Principal: | |
| Service: ecs-tasks.amazonaws.com | |
| Action: 'sts:AssumeRole' | |
| Policies: | |
| - PolicyName: 'ExecuteCommandPermissions' | |
| PolicyDocument: | |
| Version: '2012-10-17' | |
| Statement: | |
| - Effect: 'Allow' | |
| Action: [ | |
| "ssmmessages:CreateControlChannel", | |
| "ssmmessages:OpenControlChannel", | |
| "ssmmessages:CreateDataChannel", | |
| "ssmmessages:OpenDataChannel" | |
| ] | |
| Resource: "*" | |
| - Effect: 'Allow' | |
| Action: [ | |
| "logs:CreateLogStream", | |
| "logs:DescribeLogGroups", | |
| "logs:DescribeLogStreams", | |
| "logs:PutLogEvents" | |
| ] | |
| Resource: "*" |